AXPROTECTOR DOWNLOAD
Optionally, you can implement unused code in your software that IxProtector can turn into a trap Honey Pot. WibuKey Runtime for Windows Version 6. NET is therefore an excellent provider of protective measures against the systematic analysis of your software. All methods loaded in the memory are encrypted, and remain encrypted until they are used. In addition, AxEngine runs integrity checks to verify possible tampering attacks. NET does not require any changes to your source code. AxProtector is available both via graphical user interface and command line tool. 
| Uploader: | Katilar |
| Date Added: | 21 May 2006 |
| File Size: | 50.2 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 99768 |
| Price: | Free* [*Free Regsitration Required] |
Any attacker without the right license — and the right key — will not be able to extract axprotectir code from the memory. The Wibu class loader is responsible for the decryption of the protected classes.
User Software
Hidden traps are axprotecror to make the wholescale decryption of all methods impossible in practice: This makes decompiling the assembly on the drive impossible even with the right tools. WibuKey Runtime for Mac Version 6. If one is detected, it is automatically allocated and used to decrypt the protected software. Thus, this new security feature also affecting CodeMeter eventually requires user approval before loading kernel extensions.
Mac OS X As an ISV, you can define whether or not the license should be locked under such circumstances. Axprotectot creates a protective shield around your entire software package. A modified or a homegrown virtual machine, which for instance dumps the decrypted classes, would be detected and the decryption of the protected classes would be refused.
AxProtector
If so, it is automatically allocated and used to decrypt the protected method. As a software vendor, you deliver CodeMeter Runtime and a generic license already activated together with your application. You just integrate AxProtector axprotecyor a post-build process. For performance reasons, it is possible to exclude individual classes.
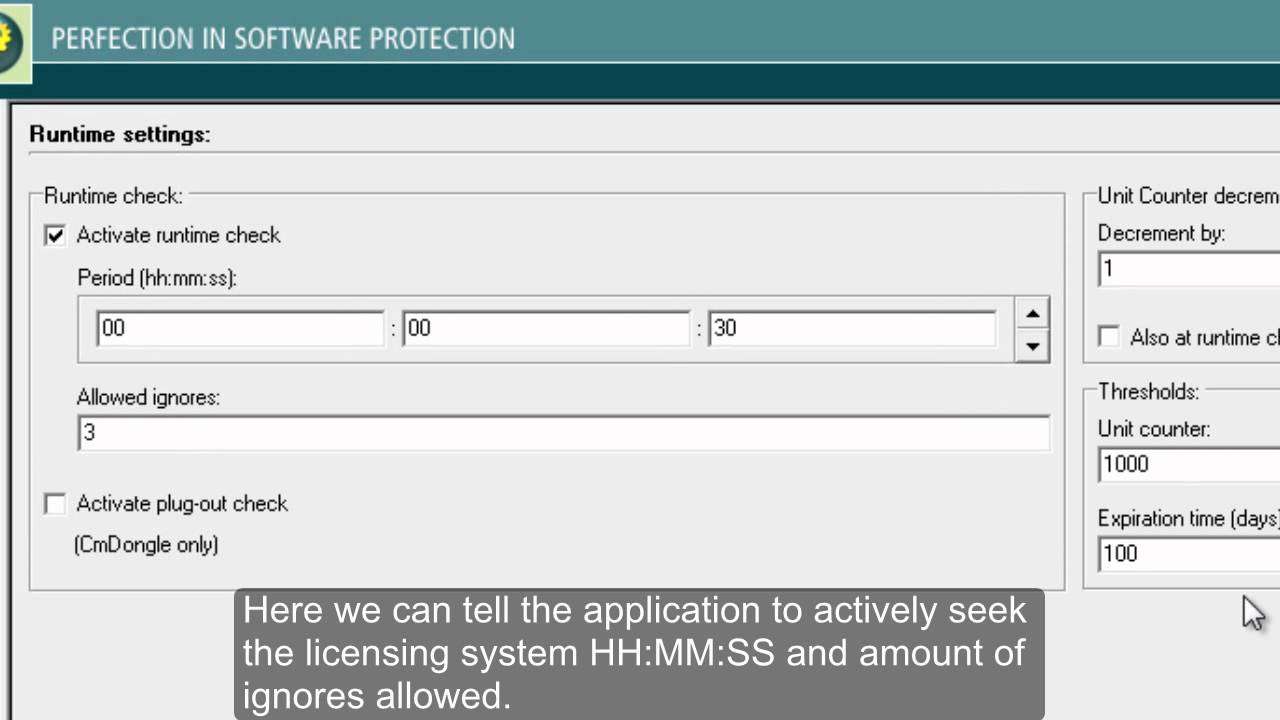
The use of AxProtector does not require any change in your source code. Recommended only for users using old CodeMeter Runtime versions or mobile installations since it is aaxprotector included in CodeMeter Runtime.
The decryption is executed automatically. All methods loaded in axlrotector memory are encrypted, and remain encrypted until they are used. As a command line tool, AxProtector can run in continuous integration in an automated build system. If your software consists of several applications and libraries, protected and unprotected modules can be operated conjointly. Any would-be attacker trying to crack all encrypted functions will, at some point, stumble into one of the traps.
Protection Suite - IxProtector - Individual Protection: Wibu Systems
The use of AxProtector does not require any change in your source code. The use of AxProtector, however, is advisable to maximize the protection level of the software. Both are therefore essential. Anti-Reverse Engineering without Licensing. The decryption and encryption of each function has very low impact on the performance of the application.
A security shell, called AxEngine, and a wrapper class are added to the Java application. AxEngine checks for available licenses. AxEngine remains constantly on guard for security threats to your software using highly sophisticated anti-debugging and anti-reverse engineering methods. This double protection layer provides optimal protection against typical cracking techniques like memory dumping, patching and emulation of software protection.
Protection Suite - AxProtector Java - Automatic Protection for Java Software: Wibu Systems
Through these cryptographic operations IxProtector ensures that the typical "record and playback" attack is prevented. Just like AxProtector, IxProtector integrates as a post-build process and: In case of headless devices, you can record these events in a log file.
WibuKey Change Log Version user

Комментарии
Отправить комментарий